Exchange/Outlook autodiscover bug exposed 100,000+ email passwords
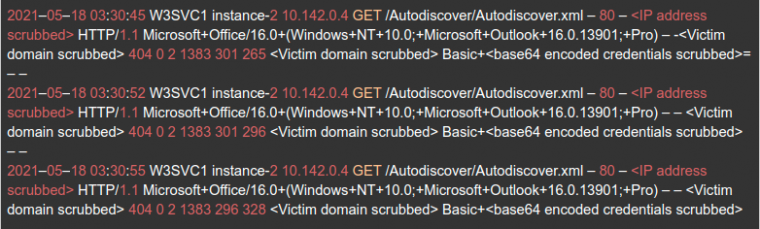
Enlarge / If you own the right domain, you can intercept hundreds of thousands of innocent third parties’ email credentials, just by operating a standard webserver. (credit: Guardicore)
Security researcher Amit Serper of Guardicore discovered a severe flaw in Microsoft’s autodiscover—the protocol which allows automagical configuration of an email account with only the address and password required. The flaw allows attackers who purchase domains named “autodiscover”—for example autodiscover.com, or autodiscover.co.uk—to intercept the clear-text account credentials of users who are having network difficulty (or whose admins incorrectly configured DNS).
Guardicore purchased several such domains and operated them as proof-of-concept credential traps from April 16 to August 25 of this year:
Autodiscover.com.br
Autodiscover.com.cn
Autodiscover.com.co
Autodiscover.es
Autodiscover.fr
Autodiscover.in
Autodiscover.it
Autodiscover.sg
Autodiscover.uk
Autodiscover.xyz
Autodiscover.online
A web server connected to these domains received hundreds of thousands of email credentials—many of which also double as Windows Active Directory domain credentials—in clear text. The credentials are sent from clients which request the URL /Autodiscover/autodiscover.xml, with an HTTP Basic authentication header which already includes the hapless user’s Base64-encoded credentials.